Antivirus

12 Steps for Stronger Ransomware Protection
Over the last few years, we have signed up hundreds of MSPs. We like to ask every new customer why they...

Building Your MSP Security Offerings
As a managed service provider (MSP), your customers already expect you to keep their networks secure....

Using MITRE ATT&CK™ in Threat Hunting and Detection
Threat hunting is the process of proactively searching for malware or attackers that reside on your network...

CIO Essential Guidance: CISO Security Threat landscape
After a year that saw the largest and fastest transformation in work patterns in history, security teams...

Microsoft Digital Defense Report
Over the past year the world has borne witness to a burgeoning cybercrime economy and the rapid rise...

The Evolution of Cybersecurity
Cybersecurity Through the Years As we look at the ever-increasing, technology-dependent cyber environment...
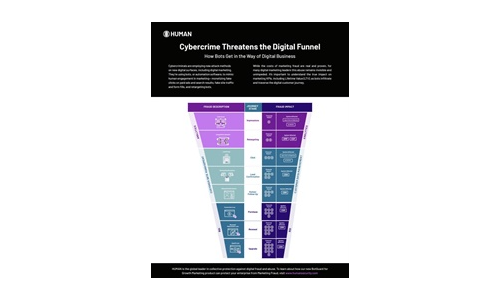
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

CMMC Compliance Guide
On January 1, 2020, the United States Department of Defense (DoD) released its Cybersecurity Maturity...

Cyber Attack Trends: Check Point’s 2022 Mid-Year Report
The war in Ukraine has dominated the headlines in the first half of 2022 and we can only hope that it...

Inside Complex Ransomware Operations and the Ransomware Economy
Ransomware operators have steadily become more sophisticated and more aligned with nation-state actors,...

Back to the Basics: Cyber Hygiene Starts with Asset Management
The challenge: managing millions of dynamic, distributed and diverse assets while maintaining high standards...

Building the foundation of a mature threat hunting program
Many organizations, especially large global enterprises, don't always have the best visibility into how...

MSP Security Best Practices: Ransomware Attack Prevention
In Datto's Global State of the Channel Ransomware Report, 4 in 5 managed service providers (MSPs) agreed...

How to protect your business from ransomware
Read this guide to gain an insight into how you can take proactive steps to keep your company's files...
Sign up for Cyber Security Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

