Latest Whitepapers

Sophos 2022 Threat Report
Interrelated threats target an interdependent world. We believe that shifting the timescale of attack...

Multi-Vector Protection
Educating users is an undeniably effective way to protect them from phishing and other malware, but it...
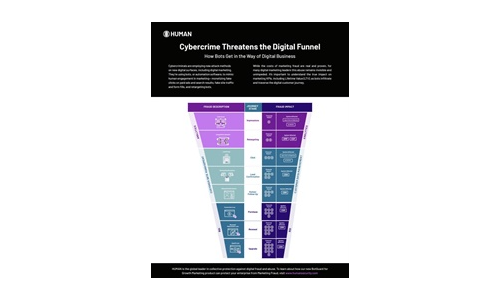
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

For digital sovereignty and transparency in the cloud
Shared use of infrastructure not only saves resources but also enables companies to push ahead with digitalisation...

2021 Norton Cyber Safety Insights Report Global Results
Prepared by the Harris Poll on behalf of NortonLifeLock, we consider: 1. Cybercrime: Incidence, Impact,...

The Passwordless Future Report
Every company has to become a technology company in order to survive and thrive in today's competitive...

Building a Cloud-Native, Hybrid-Multicloud Infrastructure
Today's world is based on the hybrid cloud. Business interactions occur on-premises, through digital...

CyberArk 2022 Identity Security Threat Landscape Report
A global report from CyberArk which shows that 79% of senior security professionals say that cybersecurity...

AI Driven Threat Defense The Next Frontier in Cybersecurity
It's undeniable that the landscape of modern cybersecurity has evolved dramatically—and at a rapid...

Forbes Study - CIO 2025
Important as the cloud already is, next-generation cloud and multicloud are expected to play even more...
Sign up for Cyber Security Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.











